Odds are high that you've worked with or actively rely on the WPA and WPA 2 Wi-Fi protocols. A newly discovered vulnerability, known as a Key Reinstallation Attack (or "KRACK Attack"), might shake your confidence.
A researcher from the imec-DistriNet research group (part of the Department of Computer Science at KU Lueven in Belgium) has discovered a critical vulnerability in the WPA and WPA 2 protocol used in Wi-Fi devices. The vulnerability not only allows for attackers to sniff packets and view sensitive data such as passwords, but also has the potential for use in man-in-the-middle attacks.
How Does a KRACK Attack Work?
The Key Reinstallation Attack does not expose encryption keys, or break passwords: it works by taking advantage of a feature in the 4-way handshake protocol that negotiates encryption keys between access points and devices before beginning a session. In particular, when the third message of this handshake protocol is received, a new encryption key is installed and then used for that session. However, since it is not unusual for packets to be lost or dropped, the access point of the network will retransmit message 3 until it receives the appropriate acknowledgement. Each time message 3 is received, the encryption key is reinstalled, the packet transmission number (nonce) is reset, and a replay counter is received.
The attack takes advantage of this by collecting and replaying message 3, forcing the reinstallation of the key and resetting the nonce, which then opens up the possibility of replaying packets, forging packets, or decrypting packets, depending on the data confidentiality method being used.
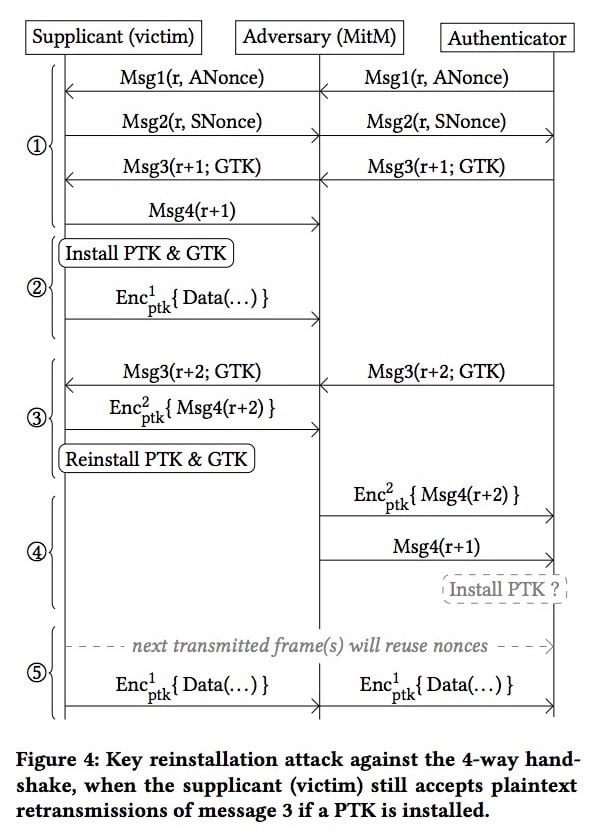
Diagram of key reinstallation attack. Image courtesy of imec-DistriNet.
What's Affected?
The 4-way handshake protocol has been proven to be secure through mathematical proofs and has been in use for over 14 years in personal and enterprise devices. The issue is not within the handshake, itself, but in the installation process for encryption keys in which it is used. This highlights that authentication security is much more encompassing than just its security protocols.
The KRACK Attack also affects the Fast BSS Transition, PeerKey, and group key handshakes. Different attacks are possible depending on the handshake being used and data-confidentiality protocol. With some combinations, only packet sniffing is possible; others make it possible for packeting forging or the injection of malicious data. So far 10 configurations have been identified with varying degrees of vulnerability and potential damage.
The researcher has identified Android and Linux devices as being the most vulnerable. In Android 6.0 devices, KRACK Attack forces the installation of a zero-encryption key.
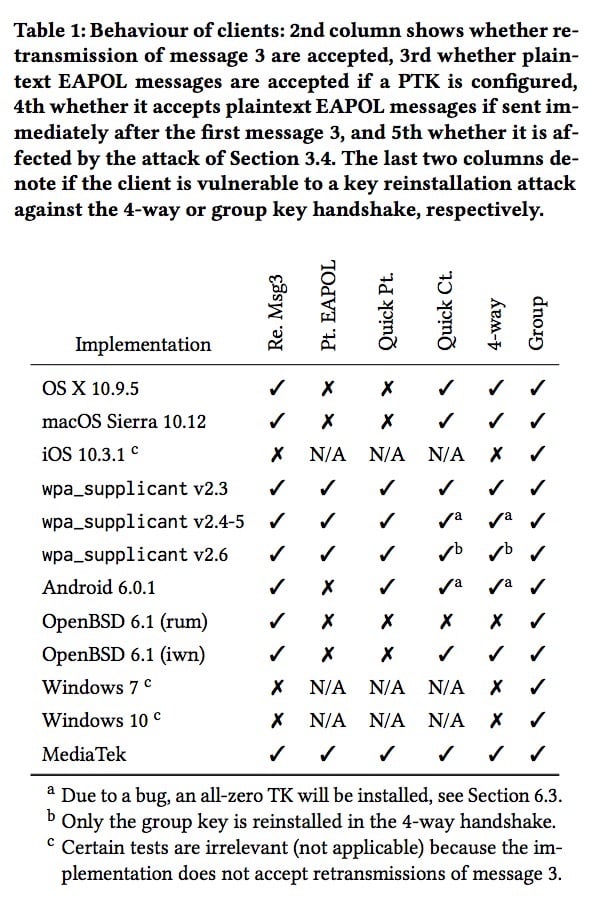
Image courtesy of imec-DistriNet.
The reprieve is that KRACK Attack requires the attacker to be in the vicinity of the access point it is targeting, and it is possible to patch devices with firmware and software updates. Some updates have already been rolled out. OpenBSD released a silent patch over the summer, a decision that could have exposed the vulnerability before other vendors had a chance to be notified before the public disclosure.
The researcher behind the discovery, Mathy Vanhoef, says that the lab began notifying vendors this past July, and then reached out to CERT/CC to disclose the vulnerability more broadly in August.
In this video below, courtesy of Vanhoef, a demonstration of the KRACK attack shows how an attacker can gain the login credentials to someone’s private account. The researcher makes a mention that he used the website Match.com to highlight how this vulnerability can give attackers access to accounts with sensitive personal information.
What You Should Do
Since nearly all Wi-Fi devices will be affected, here are your best courses of action to limit your vulnerability:
- Update software and firmware for all of your Wi-Fi enabled devices and access points (routers).
- If there is no update available for your devices, contact the vendor and perhaps limit your use of Wi-Fi until you are more confident it is secure through patching (or in a situation where your device was not using a vulnerable handshake protocol). You can see a list of vendors here.
- Do not switch to the WEP protocol. WPA 2 returns to being secure once patched.
- Changing your access point password is not necessary but can be done as an added layer of security once you have updated your firmware/software.
- Stay informed of the most recent security news that can impact your personal or corporate devices.
Feature image courtesy of imec-DistriNet.







No comments:
Post a Comment