
There are two leading methods exist for establishing mobile HMI connectivity, with one providing more cybersecurity.
Jonathan Griffith, product manager for Industrial Communications & Power Supplies at AutomationDirect, wrote an article for the September 2019 issue of Control Engineering titled Selecting HMI Remote Access Options. Here’s a summary, click on the link above for the full text.
Mobile human-machine interface (HMI) access has become a necessity for many industrial automation applications, with users expecting the same level of access whether they are remote or local. There are two typical methods for providing this access:
- Standard router without VPN
- Cloud-hosted VPN router
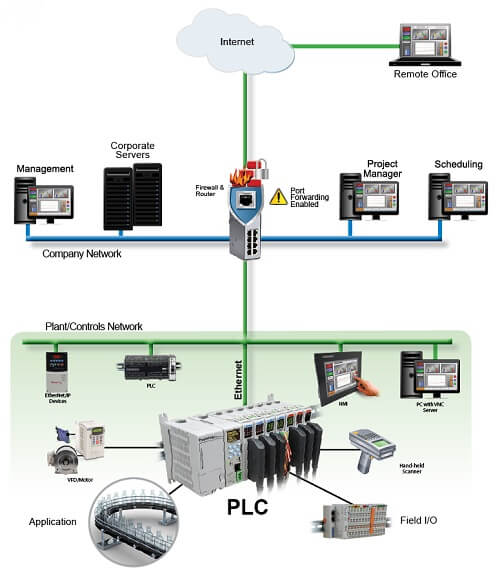
Standard Router
This is the low-cost conventional option but requires careful management and introduces cybersecurity risks since port forwarding opens “holes” in the firewall and exposes the network to external threats. Remote PC users can connect to a PC or HMI that is on-site, or they may us a mobile app.Jonathan points out shortcomings of the standard router approach:
Organizations should avoid this approach for new installations, and should convert existing installations to a more secure method.
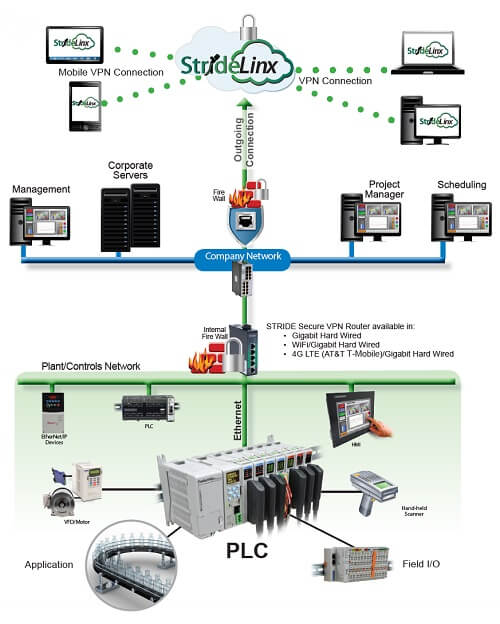
Cloud-Hosted VPN Router

The local router establishes a connection to the cloud-hosted VPN server upon startup, using outbound connections which usually require no corporate IT action. Remote users connect only upon verified request. Once both connections are made, all data passing through the VPN tunnel are secure.
Simple Router Configuration
Cloud-hosted VPNs are offered with preconfigured routers and a predefined cloud server, so non-IT staff can easily install them, as long as they know the local area network IP addresses. Other built-in advanced features such as cloud data logging and alarm notification are available.App-Based Access in Action
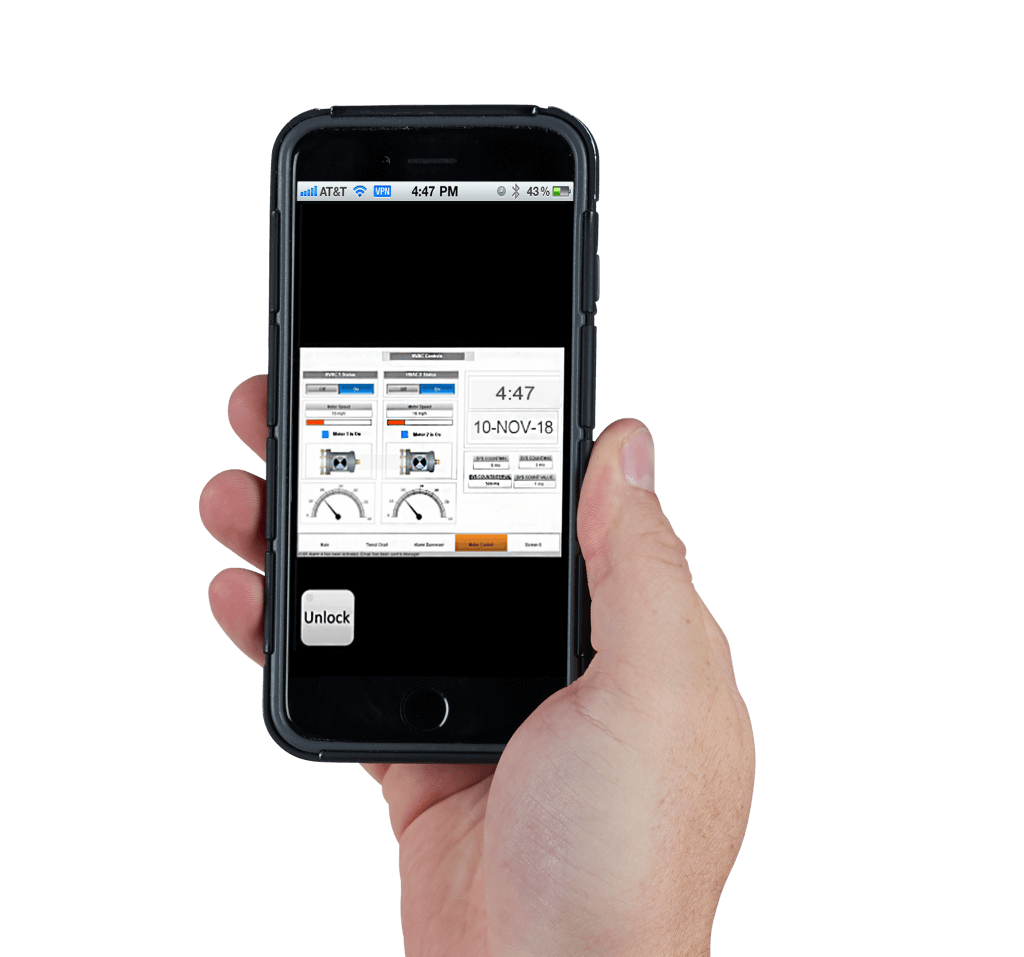
The StrideLinx service also comes
with mobile apps so users can easily access the cloud-based logged data, and use
widgets to configure dashboards for viewing live data. The C-more HMI mobile
app works securely in conjunction with the StrideLinx service.
Access to local HMIs and automation systems by mobile devices and laptops is a necessity for many OEMs and other companies. Using a cloud-hosted VPN to provide this access results in a secure system with simple installation, configuration, and maintenance.
Cloud-Based VPN Security
Access to local HMIs and automation systems by mobile devices and laptops is a necessity for many OEMs and other companies. Using a cloud-hosted VPN to provide this access results in a secure system with simple installation, configuration, and maintenance.







No comments:
Post a Comment